Is It Worth It? Let Me Work It: Calculating the Cost Savings of Proactive Security
Cost Savings Tool for NetSPI’s Solutions: External Attack Surface Management (EASM), Cyber Asset Attack Surface Management (CAASM), and Breach and Attack Simulation (BAS) as a Service
If there’s one truth that we can all agree on, it’s this: effective cybersecurity requires investment. But breaches? They’re staggeringly expensive. Many organizations are stuck playing an outdated, defensive game of triaging alerts, reacting to threats as they pop up instead of addressing vulnerabilities before attackers exploit them. That’s where modern proactive security solutions shine. Let’s discuss why upgrading your security strategy isn’t just about better protection, but also serious cost savings.
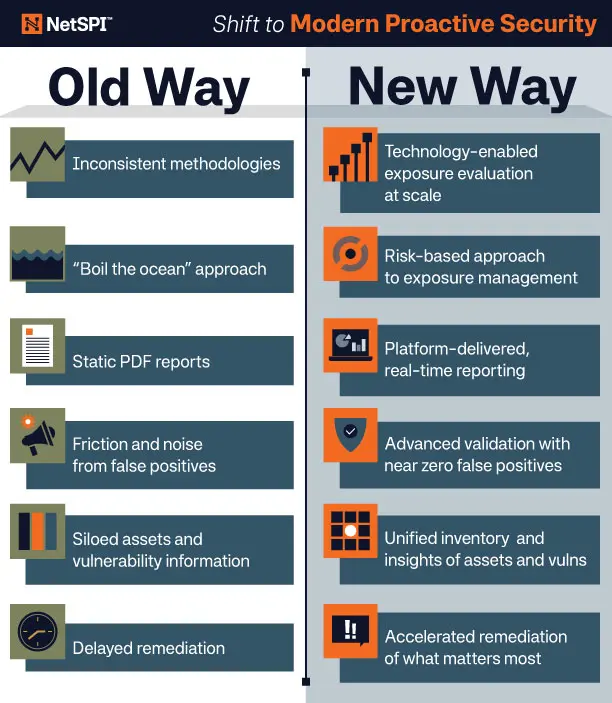
From Reactive to Proactive: A Smarter Way
Traditional security measures are full of inefficient processes, endless vulnerabilities, and late-stage panic responses. Think static PDFs and endless noise from false positives. Yikes.
Now, compare that with a proactive security approach, which aligns with a continuous threat exposure management (CTEM) framework. These modern approaches employ tech-enabled validation, deliver real-time insights, prioritize risks, and actually help you sleep better at night.
Here’s what that shift looks like in practice:
- Traditional: Static reports vs. Modern: Dynamic, real-time results
- Traditional: Boil-the-ocean triage vs. Modern: Targeted, risk-based focus
- Traditional: Manual wheel-spinning vs. Modern: Streamlined remediation of what really matters
Now for the big question every executive board asks before approving a shiny new solution: where’s the ROI?
Calculating Cost Savings for Proactive Security Solutions
The key to cost savings with modern security tools is simple math (kind of). It boils down to time saved, money spared, and risks avoided. Here are three standout solutions leading this smarter charge:
1. External Attack Surface Management (EASM)
EASM helps you understand what’s out there, beyond your perimeter. If you don’t know what you have, how on Earth can you secure it?
EASM does this by continuously scanning your external attack surface to identify hidden assets, potential exposures, and risks. Then, it prioritizes what matters most, minus all the noise, because our EASM operations team meticulously validates and prioritizes findings, eliminating false positives and reducing alert fatigue.
By combining automated verification with expert manual assessment, we provide deep context, clear attack paths, and specialized guidance for each risk. This comprehensive approach streamlines your remediation efforts, significantly reduces investigation time, and ensures your team can focus exclusively on addressing genuine critical threats—ultimately accelerating your time to remediation.
The Financial Impact:
- Breach Prevention Savings: Identifying exposures before attackers exploit them means fewer breaches, saving legal fees, recovery expenses, and reputational damage.
- Optimized Resource Allocation: Less manual triaging by your team frees up pricey, highly skilled resources to tackle other tasks on their list (which are usually a lot!).
- Insurance Cost Reduction: Proactive external monitoring can even lower your cyber insurance premiums.
- Efficient Asset Management: Automatically discovering and continuously updating your asset inventory eliminates the time-consuming process of manual asset tracking, preventing an inventory that’s outdated, which happens quickly!
Bonus? EASM keeps you one step ahead with always-on attack surface monitoring without drowning your team in busy work.

2. Cyber Asset Attack Surface Management (CAASM)
Does your organization know all the assets you own, their associated risks, and where security control coverage gaps are? Don’t worry, most don’t. Enter CAASM.
CAASM aggregates data across tools and helps you connect the dots between assets, security control coverage, and risks. Translation? Fewer blind spots and smarter decisions.
Where CAASM Saves Money:
- Asset Discovery Efficiency: Significantly reduce labor costs and eliminate redundant discovery tools through automated, continuous asset inventory management.
- Maximized Security ROI: Ensure you’re getting full value from your existing security investments by optimizing deployment coverage and eliminating protection gaps.
- Streamlined Risk Management: Achieve 85% time savings (validated by Forrester’s Total Economic Impact Study) through consolidated validation, prioritization, and contextualization of security data—turning fragmented insights into actionable intelligence without manual effort.
The cherry on top? Organizations leveraging CAASM report ROI percentages in the hundreds – 332% to be exact, according to Forrester.

3. Breach and Attack Simulation (BAS) as a Service
Adding to your proactive security lineup, here’s the heavy hitter you’ve been waiting for. BAS validates how well your security detection and defense mechanisms hold up against real-world attacker scenarios. It’s like having a highly-skilled cybersecurity team on speed dial, minus the full-time salaries and difficulty in finding the highly specialized skill set required.
How BAS as a Service Pays Off:
- Detection Assurance: Validates your security tools’ detection capabilities, ensuring you’re not caught off guard when it matters most.
- Early Threat Identification: Spots threats earlier in the cyber kill chain, helping you avoid costly ransomware incidents.
- Measurable ROI Progress: Tracks security detection improvements over time, allowing you to showcase the value of your efforts.
BAS as a Service proves its worth by validating that your security stack is detecting and preventing cyber threats and plugging gaps before attackers find them.

Why Proactive Security Solutions Are Worth It
Every dollar spent on a proactive security solution does more than just improve your cybersecurity defense; it helps your organization avoid risks, saving big on potential expenses. From reducing remediation time to preventing costly breaches, proactive solutions deliver tangible cost savings.
Stop relying on outdated practices to secure your organization. Take control, calculate the cost savings, and invest in solutions that prove their value.
Calculate the Cost Savings of Proactive Security Solutions
Need tangible numbers? NetSPI has done the heavy lifting for you. Check out our cost savings calculators for EASM, CAASM, and BAS as a Service to see exactly how they can reshape your security strategy and your budget.
What are you waiting for? It’s time to work it.
Authors:
Explore More Blog Posts
Getting Shells at Terminal Velocity with Wopper
This article introduces Wopper - a new NetSPI tool that creates self-deleting PHP files and automates code execution on WordPress using administrator credentials.

CVE-2025-21299 and CVE-2025-29809: Unguarding Microsoft Credential Guard
Learn more about the January 2025 Patch Tuesday that addresses a critical vulnerability where Kerberos canonicalization flaws allow attackers to bypass Virtualization Based Security and extract protected TGTs from Windows systems.
CVE-2025-27590 – Oxidized Web: Local File Overwrite to Remote Code Execution
Learn about a critical security vulnerability (CVE-2025-27590) in Oxidized Web v0.14 that allows attackers to overwrite local files and execute remote code execution.
