Cyber Insights From Our Security Experts
At NetSPI, we’re on the front lines of safeguarding systems — just like you. Catch up on our team’s stories, advice, and proactive security insights below.
Building a Proactive Security Playbook for Lasting Cyber Resilience
Join NetSPI and Sam Kirkman for an insightful webinar on creating a proactive security playbook. Discover actionable strategies to strengthen your cybersecurity posture and ensure lasting business resilience.

2025 Cybersecurity Trends: idk, AI I guess
Join NetSPI experts Patrick Sayler and Maril Vernon as they dive into our predictions for cyber in 2025, and offer suggestions for your business to stay ahead of these risks.

Everything You Wish You Didn’t Have to Know About Ransomware
Join NetSPI experts Ben Lister and Maril Vernon as they share actionable defense strategies you can employ now to stop ransomware before it starts.

Breach and Attack Simulation (BAS) as a Service Simulation Packs
Discover the focused attack simulations offered with NetSPI’s Breach and Attack Simulation as a Service. Choose the simulation pack that fits your unique environment.
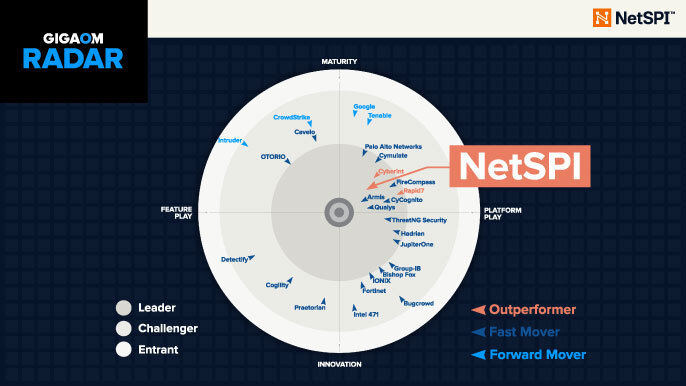
2025 GigaOm Radar Report for Attack Surface Management (ASM)
Access the 2025 GigaOm Radar for Attack Surface Management for free and see why NetSPI ASM is recognized as an Outperformer and Leader.

NetSPI Red Team Operations
Simulate real-world cyber threats with NetSPI Red Team Operations.

NetSPI Overview – The Proactive Security Solution
Strengthen security with The NetSPI Platform and solutions for continuous threat exposure management (CTEM)

Mainframe in the Spotlight: Regulatory Pressures and Real-World Attacks
Enhance your mainframe security knowledge and ensure a future-proof mainframe security posture with this on-demand session.

Strategic Attack Surface Management: Piecing Together the Puzzle
Watch this on-demand session with NetSPI experts as they discuss integrating EASM & ExPens into a unified proactive security strategy.

CAASM Best Practices: Solve Your Challenges Around Internal Asset Risk
Watch this on-demand Hacker Valley Media webinar on Cyber Asset Attack Surface Management (CAASM) best practices. Learn how to solve challenges of identifying and monitoring internal assets and their interconnected risk.

EASM Best Practices: Secure Your Network from External Threats
Watch this on-demand Hacker Valley Media webinar on External Attack Surface Management (EASM) best practices. Learn how to secure your network from external threats.

Hack Responsibly: The Hidden Hazards of CICS Application Testing
Understanding the need for comprehensive mainframe testing beyond individual risk assessments starts with this session on CICS and IMS app testing.